
How Do You Know Your Policies Are Working Correctly?
In modern networks, VLANS (virtual networks) are used to segment traffic. The problem is that IT teams cannot be physically present across dozens or hundreds of locations, so users may connect devices to the wrong network segments, interconnect VLANs, or a hacker could change security policies. For example, in hospitals, critical medical equipment may be segmented off from business or the healthcare network. In these scenarios, iStatus can be a valuable tool that’s easy to deploy and delivers huge benefits with very reasonable costs.
iStatus DDLD™ (Dynamic Data Leak Detection) is designed to allow IT administrators to set up rules which DDLD continuously tests.
When thinking about network security, you can think of an iStatus probe as a small IoT device that continuously monitors the security of a VLAN. Once deployed, the probe will listen on the network to learn and document the network configuration and devices which are present. After the learning interval, iStatus essentially stands guard and monitors the network for new devices or nefarious activities such as man-in-the-middle attacks.
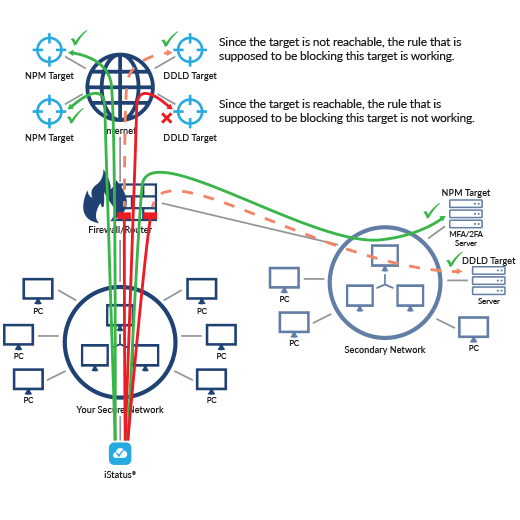
iStatus DDLD Helps Detect Security Policy Errors Or Changes
Detect when devices on your network can access things they should not be able to access – iStatus DDLD™ (Dynamic Data Leak Detection) allows you to set up rules that are tested by the iStatus probe. For example, if you have a secure PCI network, you may have cash registers that are allowed to communicate with Point-of-Sale servers, but you configure those networks so that devices on the secure network cannot communicate with Google or Facebook.
- With DDLD, you can quickly set up DDLD targets; iStatus then runs DDLD tests 24/7 to ensure that these communications are always blocked. It’s quite common to encounter errors in firewall rules which allow communications that should be prohibited. DDLD targets can be computers on a LAN, VPN, or targets on the Internet.
- DDLD can also do protocol-based testing, so if you imagine that you don’t want to allow any unencrypted HTTP traffic out of your network, you can set up HTTP-based targets, which DDLD continuously tests. DDLD performs testing and expects a normally down (fail) response from the DDLD If DDLD receives a positive response from a network target, a DDLD (data leak) event is generated, logged, and an alert is sent to you via email.
With iStatus®, you can quickly enhance network security without the need for complex servers, advanced training, or dedicated staff:

Validate if client isolation is working on a network segment, for example, a WiFi network.

Detect unexpected network security changes while iStatus continuously scans for data leaks on critical network segments.
Detect when filtering on a WAN connection for a LAN/VLAN is not working or is misconfigured. For example, a PCI-compliant network can access unintended resources on the Internet.

Detect when VLAN to VLAN traffic firewall rules are not working or are misconfigured. For example, a secure management VLAN can access an IoT VLAN, or conversely (depending on which LAN the probe is on), an IoT VLAN can access a secure management VLAN.

Detect malicious and advanced time-based attacks in instances where network infrastructure is compromised but only appears so for specific times or days.

Establish a baseline to know what devices are normally on your network, what DNS servers are in-use, and document other key security metrics such as the MAC address of the gateway.

Effortlessly document your network– iStatus provides a framework to automatically document and manage key security information across hundreds or even thousands of locations and evolve that documentation to automatically remain current and relevant.

Monitor key network parameters to detect critical changes in DNS or your default gateway, which could be indicators of compromise. Continuously test and verify connectivity, watch for data leaks, and document network events.
Built-in audit trail helps you manage network security with multiple users and know who did what and when they did it.